I just want to take this opportunity to say thanks to everyone that over the years have worked with ISA and TMG. Having myself worked with ISA and TMG since beta of ISA 2000 I can only say… You all did a fantastic job, making ISA and TMG one the best firewalls on the market. Thank you!
Tag: ISA
Issues when Migrating from ISA to TMG
Migrating from ISA to TMG is in some case quite easy, but in others it can be quite a jurney. In one of my latest cases it was indeed an interesting jurney…
So let me share some findings with you.
Moving from Standalone ISA to TMG Array.
This does not look to be a problem in theory, but…
Things you can do in a standalone ISA are sometimes not possible in a cluster.
This time it was the use of multiple subnets on a single nic. When moving to NLB you cannot have a VIP from a different subnet.
Found this out when i entered the scene day 1… And this caused the project also needing to do some IP-routing changes in the network.
Migrating Rules
Even though it is possible to export/import configurations in some scenarios. You usually want to take the opportunity to change the rules to take advantage of new features in TMG and also to clean up in the “mess” after adding rules over the years. While doing this kind of migration I have discovered many times that customer tells you one thing and the rules show something else.
You ask the cu…
“Have you made any special settings that we need to consider?”, and cu will answer “No”.
Well what you find in the rules is that a lot of them have “special non-default settings”. And when do you find this out… When users start testing! A little bit to late in other words.
The problem is that it is not a trivial task to check 100 rules in detail in order to grasp how many places have “special settings”.
Active FTP
This cu had a few FTP rules in place. They already knew which ones needed to be cleared from the “Read-Only” flag. They had learned that the hard way in ISA. But they did not know if they also required “Active FTP”. In a TMG cluster you need to “enable” Active FTP on first the enterprise level… And also on the Array level.
NLB and Procurve – Not the best combination
Using NLB to build TMG (or UAG) clusters is heavily dependent on switches used. HP Procurve has shown to not being “up to the job” in many cases.
After spending the last days helping a customer Migrate from ISA to TMG and trying to figure out how to get NLB to work in their environment I thought i should share some findings.
Unicast or Multicast
It is important to remember that TMG does not care if you use Uni- or Multicast. This is entirely a switch problem. Problem is that many network guys do not know how to pick the right one for the specific switch model at hand.
NLB in Procurve
When using typical Procurve switches (like 2800-series) you will find yourself stuck on using Unicast NLB and also having to add some static MAC-address entries in the environment.
When trying to use Multicast NLB we discovered that HP switches will not let you add Multicast MAC-addresses as static entry’s in many models.
One thing that i noted in this project is total lack of information from HP on how to integrate NLB with there different models.
Why NLB?
Many of you might say… Stop using NLB and get a HW LB instead…
In my opinion NLB should always be the first load balancing you should consider when building TMG and UAG clusters.
Why?… Simply because this is the one integrated into the product. If using any other LB you will not benefit from TMG’s integrated management. Configuring a stand-alone LB to detect service failures in TMG to cause a node-drop is not an easy task. I have also found that when using external LB you will in many cases not be able to use routed relations and will have some serious problems to get bi-directional affinity to work, especially in protocols like RPC.
ISA 2006 SP1 – Released
Finally, it’s here…. ISA 2006 SP1 was released last night.
You find it at http://www.microsoft.com/downloads/details.aspx?FamilyId=D2FECA6D-81D7-430A-9B2D-B070A5F6AE50&displaylang=en
Please read other blogposts here and also at http://blogs.technet.com/isablog/archive/2008/05/23/isa-server-2006-service-pack-1-features.aspx for information on all the new stuff in SP1.
Enjoy!
ISA 2006 and SAN Certificates
Many customers and others have been confused by the well spread rumor that ISA 2006 do not support SAN certificates like the ones used by Exchange 2007.
The confusion is often caused by the fact that they do not understand how ISA is using SSL bridging in a typical Exchange Publishing scenario.
You have to remember that SSL bridging means that there are TWO (2) separate SSL sessions going on.
Session 1: From the Client (usually on the Internet) to ISA
In this case the certificate shown by ISA is validated by the client and must satisfy the demands the client has, if no warning is to appear. If the client supports SAN certificates then you can have a SAN certificate in the ISA listener.
Session 2: From ISA to the published server (usually on the Internal network)
In this case the certificate shown by the published server needs to satisfy ISA (the original client has nothing to do with this). This means it has to be issued by a trusted CA and have a Common Name that matches the hostname on the “To” tab in the publishing rule. If this is a SAN certificate, the first SAN also needs to be the same name as the name used on the “To” tab in the publishing rule.
To summarize, ISA 2006 do support SAN certificates, but when acting as a client it can only validate the common name and the first SAN entry. This will change in SP1 (released later this summer), with SP1 ISA will as a client be able to validate any SAN entry to match the “To” used in the publishing rule.
The “great” Jim Harrison, has described this in more detail in his blog at http://blogs.technet.com/isablog/archive/2007/08/29/certificates-with-multiple-san-entries-may-break-isa-server-web-publishing.aspx
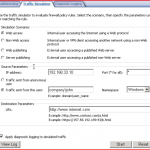
ISA 2006 SP1 – Traffic Simulator
One of the new interesting features of SP1 is the Traffic Simulator.
Using the Traffic Simulator you will be able to try out your rules to see if they match your intentions.
The Traffic Simulator is a new tab in the Troubleshooting node.
The way it works is that it “injects” the scenario into the actual engine, and therefore we can only run the simulations on a server where firewall service is running. So it’s not possible to do this remote.
The result is in my opinion still a bit “short”. It simply states the result and show the rule causing the result. If I for example have a rule that requires authentication to access internet. The results will be.
1: Traffic sent from this user:
2: Traffic sent from anonymous user:
And as you can see the information you get from the denied is only that it got stuck on the rule, but it is so far up to you to realize that it is because of authentication requirements. I have filed a change request for more info in this case, hopefully it will make it into RTM.
In all this is yet another great new feature of SP1 that i believe many customers have wanted for some time.
ISA 2006 SP1 – NEW Features
To give you all a quick overview of the new features in ISA 2006 SP1 here is a quick list. I will cover some the features in more detail in some upcoming articles. As always, since this is a beta everything is subject to change, so let’s say this is features we are “likely” to see.
When it comes to release date for SP1, the official timeframe is “late summer 2008”. And since this is built in Israel where the summer never ends (compared to here in Sweden)… Who knows how long this summer will be…I hope it will be the shortest summer in mankind so that SP1 becomes available to all of you a.s.a.p.
The list below is not ordered in any way just a list, but WHAT A LIST!!!!
| 1. | Configuration Change Tracking | Registers all configuration changes applied to ISA Server configuration to help you assess issues that may occur as a result of these changes |
| 2. | Test Button | Tests the consistency of a Web publishing rule between the published server and ISA Server. |
| 3. | Traffic Simulator | Simulates network traffic in accordance with specified request parameters, such as an internal user and the Web server, providing information about firewall policy rules evaluated for the request. |
| 4. | Diagnostic Logging Viewer | Now integrated as a tab into the Management console, this feature displays detailed events about the status of your ISA Server computer, as well as configuration and policy issues. |
| 5. | NLB Multicast | NLB now supports all three modes, Unicast, Multicast and Multicast with IGMP. |
| 6. | Cross domain KCD | Kerberos Constrained Delegation (KCD) now works in both cross-domain and cross-forest trust environments. |
| 7. | SAN certificates | Improved support for certificate with multiple SAN entries. |
| 8. | Filter RPC by UUID | Supports filtering for RPC traffic by UUID for an access rule. Previously, an access rule to RPC traffic would not be restricted by RPC interface UUID. |
| 9. | Monitor virtual memory | A new event has been created that monitors the virtual memory of the WSPSRV process. |
There are more in SP1 but i believe these are the most important ones.
When i look at this it is almost more interesting then the one we could see as news in RTM of 2006 when we compared it to 2004 SP2 (and later SP3).
Ones again… To all of you in the ISA team… Congratulations,nice work!
ISA 2006 SP1 – Change Tracking
So finally I can share with you some features of ISA 2006 SP1.
One of the great new features we will see is Change Tracking.
I have sent the product team my love for introducing this, this feature alone will make everyone hurry to get ISA2006 SP1. I also think that this will make selling ISA as a “serious” Firewall will be much easier.
In Enterprise Edition this feature is enabled on the Enterprise level.
You also have the option to require a description for all changes made.
I would suggest that you enable this as soon as the basic configuration of ISA is done and we are moving into production.
![]()
Even though you might feel tempted to raise the number of entries to a huge number, be aware that this might cause the Change Tracking, search and filtering function to be real slow.
With Change Tracking you will be able to track every change made to ISA configuration.
![]()
I will just LOVE this feature, it will make my life working with ISA so much easier. Imagine having solid proof when the customer complains that ISA “just stopped working” and they “haven’t done anything”.
If you drill down into the change you want to check out you will then see a very detailed view on what was changed.
![]()
One of the things this feature will make me stress to my customers is to use individual accounts when working with ISA, in this way we will always know “who” made this change. If we all use the administrator account, that part will be lost.
This is the first in the series of blogs I plan on SP1 features, stay in touch for more.
ISA2006 SP1 – coming soon
So finally i got my hands on SP1 of ISA 2006.
Havent had any time to test it yet, but i can promise you all a happy moment when you are able to run it. 🙂
Still NDA on the exact featurelist but let me just give you some hints about what’s in the current build.
Hopefully none of them will be removed, but as always. You never know.
– Change tracking possibility
– Multi domain/forest KCD
– Improved support for SAN certs
– Heavy improvements on troubleshooting
and much much more…
In some parts SP1 contains more news than 2006 RTM did compared to 2004 SP2.
Stay in touch and i will tell you more as soon as possible.
The Beta period is planned to be a short one, but no release date so far.