What is the plan for TMG in the future? Will it vanish or will it just be a part of the next generation where TMG and UAG become one “Unified Gateway”?
Why suddenly ask these questions you might wonder, well…
The last Gartner report, published 25 May 2011, on Secure Web Gateways presents the following Maqic Quadrant for Secure Web Gateways.
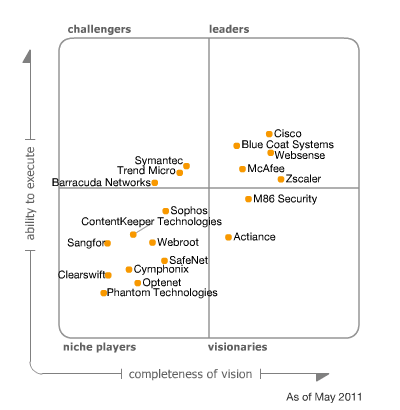
Magic Quadrant for Secure Web Gateway
As you can see it does not list TMG and the report contains the following text:
“Microsoft has informed Gartner that it does not plan to ship another full version release of its SWG product, the Forefront Threat Management Gateway (TMG). The product is effectively in sustaining mode, with Microsoft continuing to ship Service Pack (SP) updates; the next one, SP2, is planned for 3Q11. Microsoft will also continue to support TMG for the standard support life cycle — five years of mainstream support and five years of extended support. In the SWG category, TMG will become less competitive over time, since Microsoft’s goal is not to compete head-to-head with other vendors in that space. We believe that Microsoft will repurpose TMG technologies in other products and services as part of its overall cloud strategy.”
I have spent the last few days trying to get some “official” comments on this from Microsoft but has so far failed. So we can only speculate what this means.
My speculation around this is that this is part of the cloud strategy as mentioned in the Gartner report and UAG is the gateway product prepared for the cloud. My guess and speculation is that this is not the end of TMG as function but maybe as standalone product. I think we will see TMG and UAG merge into one “Unified Gateway”.
[Update 2011-05-31]
During the last 48 hours I have recieved information leading me to believe my guess and speculation above is not entirely correct. The “truth” is not yet revealed but hopefully Microsoft realize that customers and partners are waiting for clarification on the product roadmap of TMG and UAG.
[End of Update]
As soon as any official statement is presented I will add that to this post.
[Update 2012-09-17]
Important changes to Forefront product roadmaps
[End of Update]