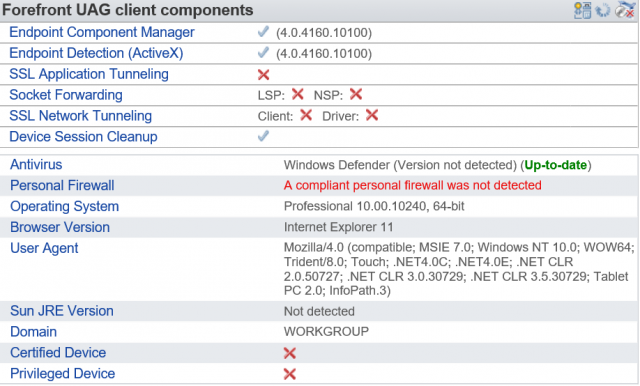
Many customers that used UAG 2010 for DirectAccess is in the process of replacing it with DirectAccess in Windows Server 2012 (or 2012 R2). One issue with this is that once UAG has been your DA server it has a hard time forgetting it.
Today I stumbled upon such a case. UAG had not been used for DA for 6 months and DirectAccess had been disabled following the official TechNet article on how to disable and enable DA in UAG.
Now however they started to clean-up some more. Removing the IP-HTTPS certificate and the IP addresses used by DA in UAG. When they did UAG failed to activate the DirectAccess configuration!
The solution to this problem is to remove a small file on the UAG server that holds information about the DA IP addresses and certificates. The file you need to remove is the uagda.config file located in the common\conf folder of your UAG installation.
After deleting the file your UAG should activate just fine again.